"K Ying" monitoring and auditing platform helps the Internet of Things "smart" to fly
Features
A push button switch is a switch that has a knob that you push to open or close the contacts. In some pushbutton switches, you push the switch once to open the contacts and then push again to close the contacts. In other words, each time you push the switch, the contacts alternate between opened and closed. These types are commonly called latching switches. There are also Non latching push button switches that only maintain the switch contacts when the switch is help in position. Once the switch is let go, the current is broken and the switch turns off. Push switches are usually a simple on-off switch.
Push On Off Switch,Small Push Button Switch,Automotive Push Switch,Miniature Push Button Switch Ningbo Jialin Electronics Co.,Ltd , https://www.donghai-switch.com
The in-depth application of information technology in the industrial field, as well as the increasing industrial control network security incidents, has pushed the development of industrial control network security industry and innovative technologies. Industrial control network security is not the same as IT security. Industrial production is extremely demanding for reliability, real-time and stability. Therefore, how to conduct real-time monitoring, real-time alarm and accurate safety audit of the industrial control system is critical if the industrial production is not affected. The Yanen network monitoring and auditing platform is such a product, which more satisfies the technical and application requirements of industrial enterprises for industrial control network security products.
Industrial control network security incidents frequency far beyond imagination <br> <br> industrial network security into public view and really get attention, began in 2010, the Stuxnet virus raid Iranian nuclear power plant incident. In fact, as early as February 1992, the Lithuanian Inalina nuclear power plant had experienced a network security crisis in the core control system. The nuclear power plant computer center employee was dissatisfied with the management and implanted a malicious program (logic bomb) in the power plant control program to make the control system function abnormal. Since the early 1990s, the importance and supervision of industrial control network security has been exposed on a global scale. Especially in recent years, the frequency of attacks against industrial-controlled network security has far exceeded the imagination of the outside world. The security threats faced by industrial control enterprises have become more diversified, and the course and intensity of attacks have gradually escalated. 
At present, the cyber security community has found more than 130 targets in the world, most of which are petrochemical, marine, military, aerospace, heavy machinery and rail transit industries, including Spain, Pakistan, United Arab Emirates, India, China, Egypt and other countries. The spear-type mail used in the attack is mainly sent to senior managers of the target organization, such as sales and marketing managers, financial and administrative managers, purchasing supervisors, engineers, and so on.
In fact, it is only the tip of the iceberg that can disclose the published IPC security incidents. The industrial security network security situation is far more serious than what is known.
Industrial control network security <br> <br> industry information Ying has become a trend of the outbreak, the control system network security is an important part. The state attaches great importance to the safety of key information infrastructure and the safety of important infrastructure, and promotes the industrialization of industrial network security. From the Ministry of Industry and Information Technology issued the No. 451 document “Notice on Strengthening Information Security Management of Industrial Control Systems†in 2011, clearly stipulated the measures to strengthen the safety management of industrial control information systems in key areas; by February 27, 2014, the Central Network Security and Informatization Leading Group The announcement was established, marking that cybersecurity has been upgraded to the national strategic level. On November 3, 2016, the Ministry of Industry and Information Technology officially released the “Industry and Information Technology Department on Printing and Distributing the Guidelines for Information Security Protection of Industrial Control Systems†(Jianxin Soft Letter [2016] No. 338), which standardized the technical requirements for industrial control information security. .
Benefiting from policy support, companies engaged in IIoT industrial IoT security and industrial control network security have sprung up. As the mainstay of industrial development and technological innovation, the emergence of these network security enterprises has further promoted the development of industrialization and more satisfied the technical and application requirements of industrial enterprises for industrial control network security products. From the perspective of industrial enterprises, with the development of industrial informatization and the transformation and upgrading of enterprises, the awareness of network security of industrial enterprises has increased, and enterprises have gradually realized the importance and necessity of industrial control network security, and the safety of industrial control networks deployed on industrial sites. Product demand has increased accordingly.
Monitoring of industrial network security audit is the starting point should be normalized <br> <br> combination of network engineering PETER Well the last three years of implementation experience, the defense should be structured network security protection of industrial safety, security body, behavioral safety, security genes plus Time persistence begins in five aspects. In the network security ecological closed loop, detection and evaluation is the basis of industrial control network security, and real-time monitoring and real-time alarm and effective security audit are the entry points of industrial control network security, and should become the normalization of industrial enterprise network protection.
In view of the particularity of the industrial control network, there are many different elements from traditional information security, such as the use of protocols and application scenarios. The company has proposed and researched products that are conducive to the discovery of security incidents on the industrial control network - "K Eagle" monitoring. The audit platform is a real-time monitoring, real-time alarm, and security audit system designed specifically for industrial control networks. Through specific security policies, it can quickly identify illegal operations, abnormal events, and external attacks. In addition to the deep analysis function, the “K Ying†monitoring audit can cover the industrial protocols of most industrial control companies in a high degree, and can also display the current on-site network and equipment operation status to users in real time, and provide evidence for real-time alarms and event traceability of emergencies. It is especially important for remote understanding of on-site production.
Combined with the industrial site environment and industrial control features, the product's innovation in technology and design is more in line with industrial network security protection needs:
Bypass monitoring audit: Bypass monitoring audit does not affect the normal operation of the original industrial production;
Avoid adding threat ports: deployed on the switch mirror port, using one-way data capture to avoid other threats;
No delay transmission of production safety events: 0 delay to ensure the real-time control of industrial control system instructions, timely on-site safety issues, to ensure effective and accurate production.
Avoid adding points of failure: no increase in the point of failure due to the addition of safety equipment;
Typical application scenarios are as follows: 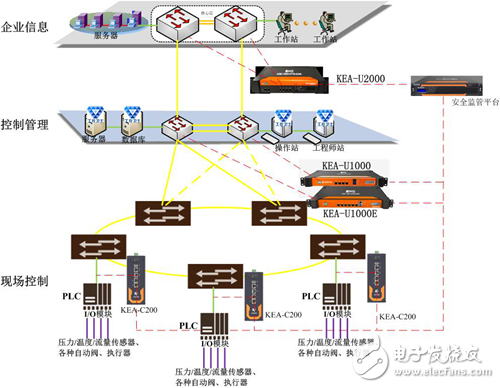
User value:
Real-time monitoring of the whole network to ensure normal production: real-time monitoring of network data and events, real-time warning, help users to grasp the operation status of industrial control network in real time, and ensure normal production.
Network security audit, easy for history tracking: Provide behavior auditing, content auditing, protocol auditing, traffic auditing for all activities existing in the network, and generate complete records for event tracing.
Unknown device monitoring, timely threat discovery: Real-time alarms for unknown device access in industrial control network systems, and rapid detection of illegal access in industrial control network systems.
Defense strategy recommendations, improve the defense system: According to the monitoring results, provide defense strategy recommendations to help users build a suitable exclusive industrial control network security defense system.
Conclusion: With the development of the industrial control network security market, the “K Ying†monitoring and auditing platform has spawned more products that meet the needs of the segmented industries. As the leader in the field of industrial control information security, Yanen Network will continue to innovate and create a rich “K Ying†monitoring and auditing platform, making it a standard product for industrial control network security protection, and winning a broader service with professional services. market.