Automobile safety performance urgently needs to upgrade the embedded system to guard
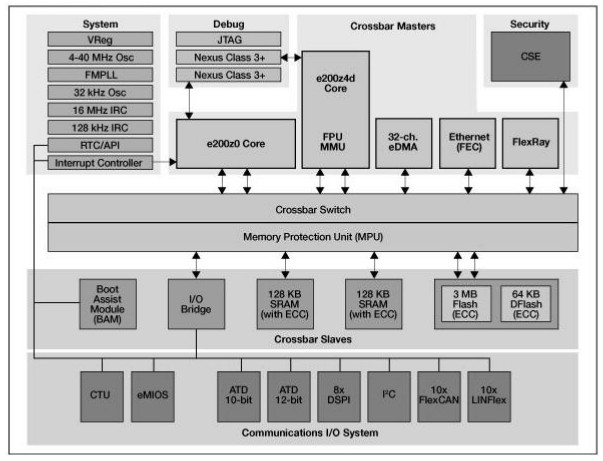
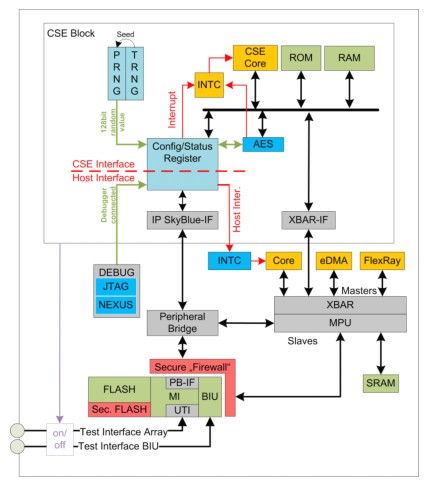
1 Summary The safety of the car cannot be separated from security. For example, only through the security measures to protect the integrity and authenticity of the firmware of the brake ECU (electronic control unit) can the safety of the car's brake be ensured and the threat of malicious modification of the firmware and the like be prevented. Another example of security requiring security is the onboard network, which transmits critical data from the sensor to the brake ECU. Only through security measures to prevent the on-board network from defending against threats such as data modification, message injection, and denial of service can the brake ECU receive the correct sensor value in time. People want to launch an open software platform such as Android ™ or MeeGo ™ in the car, and a new safety and security challenge has emerged: in order to allow users to interact with the button and extract the current speed, remaining fuel, For information such as mileage, location, etc., the software platform and its applications need to participate in onboard vehicle communication. However, it is necessary to protect the car from application failures. Virtualization and running the software platform (including applications in the sandbox) are one of the security measures to achieve protection in the ECU. Under these circumstances, security measures have improved safety. However, in some cases, security requirements and security requirements contradict each other. For example, to protect the confidentiality of firmware, the debug port of the microcontroller is disabled irreversibly after the ECU is assembled. If the repair is due to a malfunction of the ECU, the disabled debug port will prevent the root cause analysis within the microcontroller. In particular, it cannot be analyzed for software, configuration, or hardware defects. The emerging functional safety standard ISO26262 requires the investigation site to be repaired in order to detect system failures and then initiate the recall. Only with the help of methods such as intelligent security life cycle and safety debugging, can we meet the safety needs and analyze the root cause when returning to the site for repair. This article introduces the main safety features of advanced microcontrollers and how to apply these features to ensure vehicle safety: specifically, this article covers safe boot, component protection and virtualization. In addition, this article also outlines solutions for ensuring safety and handling on-site repairs. 2 Introduction In the past few years, the safety features of automotive microcontrollers (MCUs) have become increasingly important. This trend is driven by traditional security use cases, such as anti-theft devices or component protection, which can prevent cars from being stolen. However, new use cases such as vehicle-to-vehicle communication and higher safety requirements have also increased safety requirements. For these use cases, the automotive industry began to develop specifications such as the Secure Hardware Extension (SHE) functional specification, or the security architecture proposed by the EVITA project. Semiconductor companies began to implement these specifications in a new generation of microcontrollers. One of the first results of this work is the Qorriva MPC564xB / C series, which implements an easy-to-use security module to meet SHE specifications. Car processors such as the i.MX series are rooted in the consumer electronics market and have now entered the automotive market to implement the most advanced driver infotainment systems. These processors provide hardware security and support complex digital rights management systems. 3 Qorivva MPC564xC / B series The QorivvaMPC564xC / B series of 32-bit microcontrollers are aimed at safe, new generation high-end automotive body control modules (BCM) and gateway applications. It provides a high degree of integration and can meet the growing demands of OEMs and first-tier customers for enhanced feature sets and increased memory space. From a security perspective, MPC564xC / B includes a Cryptographic Services Engine (CSE). CSE is a set of cryptographic hardware features that allows for the safe and trusted transmission of information between ECUs. The MPC564xC / B series also has dual Power Architecture® core options, providing nearly 300 DMIP processing functions and low-power standby / waiting modes to help reduce power consumption. It also has an extensive set of communication peripherals for docking with BCM / gateway modules Extensive subsystems. In addition, these scalable devices are supported by the enabling ecosystem, which includes software drivers, operating systems, and configuration code to help you quickly deploy your design. Figure 1 shows the block diagram of Qorivva MPC564xC / B. Figure 1: Qorriva MPC564xC / B block diagram 3.1 Security features of CSE Cryptographic Service Engine (CSE) is a cryptographic hardware module integrated in Qorriva MPC5464. The CSE module implements the safety functions described in the Safety Hardware Extension (SHE) functional specification. Figure 2 shows the block diagram of the CSE module. Figure 2: CSE block diagram The CSE design includes a host interface with a set of memory-mapped registers that are used by the CPU to initiate encrypted commands. In addition, there is a system bus interface that allows CSE to directly access system memory. Here, the behavior of the CSE module is similar to any other host. Through the host interface, the application program can configure and control the CSE, for example, make the CSE enter a low power consumption mode, interrupt the completed command processing or suspend the command processing. Status and error registers will provide in-depth system information. For a complete list of CSE commands, please refer to the MPC564xC / B Reference Manual [3]. Two dedicated system flash memory blocks are used by CSE for encryption key storage. No other host can access these modules from the system, so these modules are called secure flash. The AES block of the CSE module is connected as a slave to the internal bus of the CSE module. It handles encryption / decryption and provides a message authentication code (CMAC) based on cipher text. The CMAC function is used to implement a secure boot mechanism. The random number generator includes a pseudo-random number generator (PRNG). The seeds of PRNG are generated by TRNG. The CSE control accesses the secure flash memory from the outside through the test interface. This function is used during the production process and is also used for field repair verification. When the Qorriva MPC564xC / B semiconductor is shipped from Freescale, the test interface is open, and the interface will be closed when the encryption key is programmed into the device. The quality engineer can use the CMD_DEBUG function described in the SHE specification to reopen the test interface. The CMD_DEBUG function will delete all data in the secure memory before authorizing access to the test interface. An input parameter of the CMD_DEBUG function is MASTER_KEY, which is a single pre-programmed 128-bit value, which is different for each device. Only the knowledge carrier of MASTER_KEY can successfully start the CMD_DEBUG function. After attaching the debugger, you can individually disable the encryption key. Disabling the key means that the CSE can use the key to reject any encryption function. 3.2 Some use cases supported by CSE CSE helps achieve the following use cases or systems: • Anti-theft device • Component protection • Secure flash programming • Data set protection (eg driving mileage) • Prevent chip adjustment There are still many use cases, and more will appear in the future. The following paragraphs describe two important use cases in detail. 3.2.1 Secure boot and chain of trust When the MPC564xC / B is reset, the CSE will automatically verify the array in public flash memory. The base address and length of the array are specified by the developer. The same address entry is used as the first instruction address of the main core. The CSE calculates the CMAC value outside the array and compares it with the pre-calculated value stored in secure memory. According to the comparison results, CSE will provide encryption services or not. Because the system flash memory is large-MPC564xC / B provides up to 3MB of flash memory-so the secure boot process may take some time. For this reason, developers can set up a chain of trust. In this case, the flash memory verification step is divided into several sub-steps. The first flash block is verified by the CSE, as described above; verification of the following flash blocks must be triggered by the verified code of the main core through the program. 3.2.2 Component protection The component protection function prevents a single ECU from being removed from the car and reused in other cars. Usually the purpose of stealing a car is to resell a single ECU to the parts market. OEMs can now solve several problems with a security component protection system. First, car manufacturers can reduce the number of stolen cars; second, they can prevent negative effects on reputation and configuration; third, they can protect their after-sales business. The component protection system based on CSE seems to be able to achieve the above purpose. The most valuable ECU will contain a microcontroller with a CSE module. One or more main ECUs can be assigned by design, or a specific algorithm can be used for dynamic assignment. The main ECU will poll all other ECUs of the component protection system and ask for a specific answer (eg encrypted unique ID). In this case, only the ECU with the correct secret key can send back a valid response. In addition, the main ECU can use all ECU databases assembled in a particular car to cross-check the received ID. When using the car, regular component inspections can be carried out. If the master node detects an unauthorized ECU in the automotive network, it can react.
Win3 Group, which established in 2003, specializes in design and production and research and development of intelligent mining LED lighting/Miners Headlamp/ Lighting Fixtures/street lamp/flexible stripe light etc.
With many years of
dedicated R&D in the lighting technology field, Win 3 produces mining cap
lamps that reduce visual fatigue while maintaining high light output levels.
Win 3 offers a 16
month warranty against any defective components or workmanship.
Lighting Fixtures Led Chandelier,Rustic Light Fixtures,Industrial Light Fixtures,Fluorescent Light Fixture ZHEJIANG HUACAI OPTIC-TECHNOLOGY CO LTD , https://www.win3safety.com